
Overview
I am CEO and co-founder of Crosslayer Labs (and a Y-Combinator W26 founder), where I lead the company to build solutions for web infrastructure security.
Previously I was a research software engineer at Princeton University in the CS and ELE departments. I primarily worked under professors Prateek Mittal (Chief Scientist at Crosslayer Labs) and (now Princeton University provost) Jennifer Rexford on Internet security and privacy. I am an inventor and key advocate of Multi-Perspective Issuance Corroboration (MPIC) which helps protect HTTPS connections from BGP attacks. As an industry-wide standard, MPIC helps secure the issuance of all ~8 million HTTPS certificates signed every day and is mandated by the CA/Browser Forum.
I am also a founder of the Open Multi-Perspective Issuance Corroboration Project (Open MPIC) which provides open-source implementations of MPIC which are used in production by several leading CAs.
Impact
Real-world impact is what motivates me to do research. To this end, I always strive to have my research deployed. Below are several examples of initiatives I have lead that are currently deployed in the real world.
-

Image credit: Cloudflare
Inventing Multi-Perspective Issuance Corroboration (MPIC)
MPIC (sometimes also referred to as Multi-Perspective Domain Validation or MPDV) is a technology deployed by Certificate Authorities (or CAs) that helps protect TLS certificate issuance from equally-specific BGP attacks.
- In 2016 I coded the first ever MPIC implementation and in 2018 I was lead author of the paper that introduced MPIC.
- My research was a key factor leading to MPIC getting deployed at the world's largest web PKI CA Let's Encrypt in Feb 2020 where it has since secured the issuance of over one billion certificates.
- MPIC has also been deployed at Google Trust Services (the CA responsible for signing certificates for Google services including google.com itself) and is implemented by CloudFlare.
- Following several presentations I made to the CA/Browser Forum, I participated in a work team to draft language to mandate MPIC in the CA/Browser Forum's Baseline Requirements. This draft was endorsed by the Chrome Root Program, Let's Encrypt, and Fastly as Ballot SC-067 which mandated MPIC industry wide.
- The CA/Browser Forum (which governs all web PKI certificate issuance) unanimously voted in favor Ballot SC-067. As a result, since March 15, 2025, MPIC is mandated for the issuance of all publicly-trusted server certificates.
- MPIC secures the issuance of ~8 million certificates a day and provides improved security to the millions of websites and billions of users that rely on HTTPS and the WebPKI.
One aspect of MPIC I am particularly proud of is that Princeton University has given MPIC to the public domain. This supports MPIC's continued adoption and maximizes its potential to improve Internet security.
-
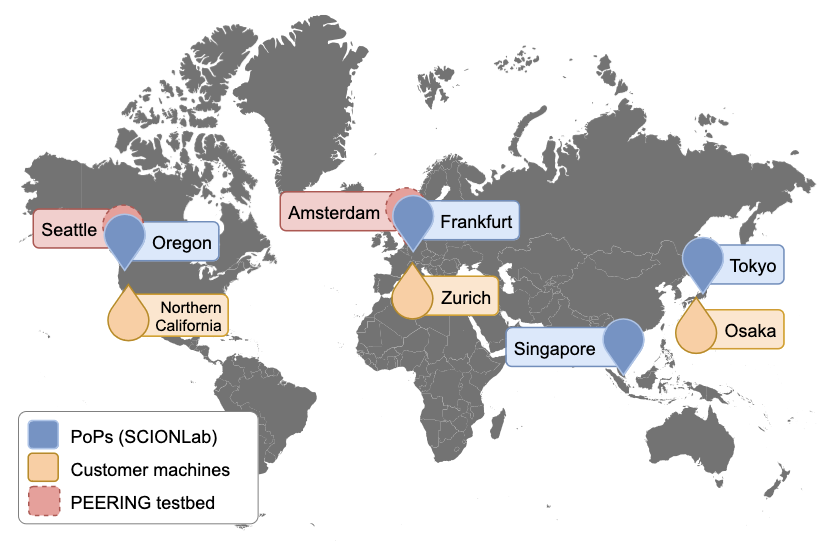
Image credit: USENIX Association
Developing the Secure Backbone Autonomous System (SBAS)
SBAS brings the advantages of new emerging secure Internet architectures to hosts on today's networks already-deployed hardware.
- I was lead author of the paper that introduced SBAS.
- A prototype SBAS deployment is operational with four nodes spread across the world and operates out of AS 400065.
- SBAS is planned to be deployed in production on the SCION Research and Education Network
-

Image credit: SCION Architecture
Bringing SCION, a Next-Generation Internet Architecture, to Princeton University
SCION is a Next-Generation Internet Architecture that offers improves security and performance over traditional inter-domain IP routing. SCION is deployed in production networks like the Secure Swiss Finance Network and has recently started an international research and education network that Princeton University is a part of.
- I was a key part of an initiative lead by the Princeton Inspire Research Group to develop secure layer-2 link over Internet2's Advanced Layer 2 Service (AL2S) from the SCION R&E Network's interconnects in Virginia, Chicago, and Seattle to the Princeton campus.
- I administer the SCION Router on the Princeton University campus (AS 88 in ISD 71) which provides native SCION connectivity to connected devices.
- I also lead the deployment of the SCION Bootstrapper at Princeton University which offers zero-configuration native SCION connectivity to hosts Princeton's network.
-
Founding the Open MPIC Project
I am a founder and lead developer on the Open MPIC project which offers several open-source implementations of MPIC that are used in production.
- Several prominent CAs use Open MPIC for their production MPIC implementation.
- The project provides a core MPIC library (that can be extended to implement MPIC in any environment) and several fully-implemented deployments including a serverless deployment and a container-based deployment.
- The Open MPIC project hosts the draft MPIC API specification which is being developed in collaboration with CloudFlare and submitted to the IETF.
-

MPIC Labs
I am a founder of MPICLabs which provides guidance on MPIC deployment and has already helped Google Trust Services optimize their MPIC deployment.
Policy Impact
I partake in several initiatives aimed at moving industry, national, and international policy in a more informed direction.
Membership in the CA/Browser Forum
I was selected to join the Server Certificate Working Group of the CA/Browser Forum as an interested party where I contribute to industry-wide certificate policy including the CA/Browser Forum's Baseline Requirements which regulate the issuance of all publicly-trusted TLS certificates.- Ballot SC-067: Require Multi-Perspective Issuance Corroboration I am an author of this ballot which mandated all CAs use MPIC. The ballot was proposed by Chris Clements and Ryan Dickson of Google (Chrome Root Program) and endorsed by Aaron Gable (ISRG / Let’s Encrypt) and Wayne Thayer (Fastly). It passed with unanimous support among CAs and Browsers.
- Ballot SC-085: Require DNSSEC for CAA and DCV Lookups I authored this ballot which requires all CAs to validate DNSSEC, and it was proposed by Clint Wilson (Apple) and endorsed by Wayne Thayer (Fastly), Dimitris Zacharopoulos (HARICA), and Ryan Dickson (Chrome). The ballot passed making DNSSEC validation a standard for the entire CA industry. This brings significantly improved security to millions of DNSSEC domains.
- Ballot SC-088: Persistent DNS Change I am an author of the Internet Draft adopted by the IETF ACME working group that implements this method in the ACME protocol. I also provided input on this ballot and published a whitepaper detailing its security properties which helped it gain critical certificate consumer support at the CA/Browser Forum.
IETF LAMPS Working Group
I participate in the IETF LAMPS working group where I am the author of an adopted Internet Draft: draft-ietf-lamps-caa-security. This draft is undergoing standardization by the LAMPS working group for eventual publication as an Internet Standard by the IETF (i.e., Standards Track RFC). The draft proposes a new tag for CAA DNS records that lets domain owners require cryptographically-secure certificate issuance.Chrome Root Program's Multi-Perspective Issuance Corroboration Work Team
I was a key contributor to the work team organized by the Google Chrome Root Program that developed standards for industry-wide adoption of MPIC. The resulting work ultimately became CA/Browser Forum Ballot SC-067 that was adopted by the CA/Browser Forum in a unanimous vote.Princeton CITP and University of Chicago's Response to the FCC
I worked with a cross-institutional team of top BGP researchers from Princeton's Center for Information Technology and Policy (CITP) and the University of Chicago to publish a response to the FCC's inquiry on routing security (Docket No. 22-90) which was cited by the DoD and DOJ.
https://citpsite.s3.amazonaws.com/uploads/FCC+BGP+Security+Comment-3.pdfBITAG Report on the Security of the Internet’s Routing Infrastructure
As part of the BITAG working group on Routing Security, I worked with other industry leaders on writing a technical report about the current state of routing security. https://www.bitag.org/Routing_Security.php
Click here to download my full CV.
Publications
-
 Henry Birge-Lee, Sophia Yoo, Benjamin Herber, Jennifer Rexford, and Maria Apostolaki. 2024. TANGO: Secure Collaborative Route Control across the Public Internet. In Proceedings of the 21st USENIX Symposium on Networked Systems Design and Implementation (NSDI ’24). USENIX Association, Baltimore, MD. https://www.usenix.org/conference/nsdi24/presentation/birge-lee Winner of the 2025 IRTF Applied Networking Research Prize
Henry Birge-Lee, Sophia Yoo, Benjamin Herber, Jennifer Rexford, and Maria Apostolaki. 2024. TANGO: Secure Collaborative Route Control across the Public Internet. In Proceedings of the 21st USENIX Symposium on Networked Systems Design and Implementation (NSDI ’24). USENIX Association, Baltimore, MD. https://www.usenix.org/conference/nsdi24/presentation/birge-lee Winner of the 2025 IRTF Applied Networking Research Prize
-
 Henry Birge-Lee, Liang Wang, Daniel McCarney, Roland Shoemaker, Jennifer Rexford, and Prateek Mittal. 2021. Experiences Deploying Multi-Vantage-Point Domain Validation at Let’s Encrypt. In Proceedings of the 30th USENIX Security Symposium (USENIX Security ’21). USENIX Association, Vancouver, CA. https://www.usenix.org/conference/usenixsecurity21/presentation/birge-lee Runner up for the 2022 Caspar Bowden PET Award. Finalist in the CSAW’21 Applied Research Competition
Henry Birge-Lee, Liang Wang, Daniel McCarney, Roland Shoemaker, Jennifer Rexford, and Prateek Mittal. 2021. Experiences Deploying Multi-Vantage-Point Domain Validation at Let’s Encrypt. In Proceedings of the 30th USENIX Security Symposium (USENIX Security ’21). USENIX Association, Vancouver, CA. https://www.usenix.org/conference/usenixsecurity21/presentation/birge-lee Runner up for the 2022 Caspar Bowden PET Award. Finalist in the CSAW’21 Applied Research Competition -
 Henry Birge-Lee, Yixin Sun, Anne Edmundson, Jennifer Rexford, and Prateek Mittal. 2018. Bamboozling Certificate Authorities with BGP. In Proceedings of the 27th USENIX Security Symposium (USENIX Security ’18). USENIX Association, Baltimore, MD, 833–849. https://www.usenix.org/conference/usenixsecurity18/presentation/birge-lee Runner up for the 2020 Caspar Bowden PET Award.
Henry Birge-Lee, Yixin Sun, Anne Edmundson, Jennifer Rexford, and Prateek Mittal. 2018. Bamboozling Certificate Authorities with BGP. In Proceedings of the 27th USENIX Security Symposium (USENIX Security ’18). USENIX Association, Baltimore, MD, 833–849. https://www.usenix.org/conference/usenixsecurity18/presentation/birge-lee Runner up for the 2020 Caspar Bowden PET Award. -
 Henry Birge-Lee, Yixin Sun, Anne Edmundson, Jennifer Rexford, and Prateek Mittal. 2017. Using BGP to acquire bogus TLS certificates. Talk Abstract in Hot Topics in Privacy Enhancing Technologies (HotPETS ’17). Minneapolis, MN. https://www.petsymposium.org/2017/papers/hotpets/bgp-bogus-tls.pdf Winner of the 2017 HotPETS Best Talk Award
Henry Birge-Lee, Yixin Sun, Anne Edmundson, Jennifer Rexford, and Prateek Mittal. 2017. Using BGP to acquire bogus TLS certificates. Talk Abstract in Hot Topics in Privacy Enhancing Technologies (HotPETS ’17). Minneapolis, MN. https://www.petsymposium.org/2017/papers/hotpets/bgp-bogus-tls.pdf Winner of the 2017 HotPETS Best Talk Award -
 Seungju Lee, Mona Wang, Watson Jia, Qiang Wu, Henry Birge-Lee, Liang Wang, and Prateek Mittal. 2026. Evaluating connection migration based QUIC censorship circumvention. In Proceedings of the 26th Privacy Enhancing Technologies Symposium (PETS '26). Calgary, Canada. https://petsymposium.org/2026/paperlist.php Winner of the Andreas Pfitzmann Best Student Paper Award
Seungju Lee, Mona Wang, Watson Jia, Qiang Wu, Henry Birge-Lee, Liang Wang, and Prateek Mittal. 2026. Evaluating connection migration based QUIC censorship circumvention. In Proceedings of the 26th Privacy Enhancing Technologies Symposium (PETS '26). Calgary, Canada. https://petsymposium.org/2026/paperlist.php Winner of the Andreas Pfitzmann Best Student Paper Award - Grace H. Cimaszewski*, Henry Birge-Lee*, Liang Wang, Jennifer Rexford, and Prateek Mittal. 2023. How Effective is Multiple-Vantage-Point Domain Control Validation? In Proceedings of the 32nd USENIX Security Symposium (USENIX Security ’23). USENIX Association, Anaheim, CA, 5701--5718. https://www.usenix.org/conference/usenixsecurity23/presentation/cimaszewski *Both authors contributed equally to this work.
- Henry Birge-Lee, Ari Brown, Christine Guo, Cyrill Krähenbühl, Sohom Pal, Liang Wang, and Prateek Mittal. 2025. A Framework to Evaluate MPIC Security using Real-World BGP Announcements. In Proceedings of the 2025 ACM on Internet Measurement Conference (IMC ’25). Madison, WI.
- Felix Stöger, Henry Birge-Lee, Giacomo Giuliari, Jordi Subirà-Nieto, and Adrian Perrig. 2025. BGP Vortex: Update Message Floods Can Create Internet Instabilities. Accepted to appear in the Proceedings of the 34th USENIX Security Symposium (USENIX Security ’25). USENIX Association, Seattle, WA. https://www.usenix.org/conference/usenixsecurity25/presentation/stoeger
- Henry Birge-Lee, Joel Wanner, Grace H. Cimaszewski, Jonghoon Kwon, Liang Wang, François Wirz, Prateek Mittal, Adrian Perrig, and Yixin Sun. 2022. Creating a Secure Underlay for the Internet. In Proceedings of the 31st USENIX Security Symposium (USENIX Security ’22). USENIX Association, Boston, MA, 2601--2618. https://www.usenix.org/conference/usenixsecurity22/presentation/birge-lee
- Henry Birge-Lee, Liang Wang, Jennifer Rexford, and Prateek Mittal. 2019. SICO: Surgical Interception Attacks by Manipulating BGP Communities. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security (CCS '19). Association for Computing Machinery, New York, NY, USA, 431–448. DOI:https://doi.org/10.1145/3319535.3363197
- Yixin Sun, Maria Apostolaki, Henry Birge-Lee, Laurent Vanbever, Jennifer Rexford, Mung Chiang, and Prateek Mittal. 2021. Securing Internet Applications from Routing Attacks. Communications of the ACM (CACM) 64, 6 (June 2021), 86–96. https://dl.acm.org/doi/10.1145/3429775
- Henry Birge-Lee, Maria Apostolaki, and Jennifer Rexford. 2022. It takes two to tango: cooperative edge-to-edge routing. In Proceedings of the 21st ACM Workshop on Hot Topics in Networks (HotNets '22). Association for Computing Machinery, New York, NY, USA, 174–180. https://doi.org/10.1145/3563766.3564107
- F. Wirz, M. Gartner, J. van Bommel, E. Moghadam, G. Cimaszewski, A. He, Y. Zhang, H. Birge-Lee, F. Kottmann, C. Krähenbühl, J. Kwon, K. Mavromati, L. Wang, D. Bertolo, M. Canini, B. Cho, R. Ferreira, S. Green, D. Hausheer, J. Hur, X. Jia, H. Lee, P. Mittal, O. Oaiya, C. Park, A. Perrig, J. Sobieski, Y. Sun, C. Wang, K. Wierenga. 2025. Reaching Escape Velocity for Layer-3 Innovation: Fueling Deployment of a Next-generation Internet Architecture. Accepted to appear in Proceedings of the ACM SIGCOMM 2025 Conference (SIGCOMM '25). Association for Computing Machinery, New York, NY, USA
- Henry Birge-Lee, Maria Apostolaki, Jennifer Rexford. 2025. Global BGP Attacks that Evade Route Monitoring. In Proceedings of the 26th Passive and Active Measurement Conference (PAM '25). Springer-Verlag, Berlin, Heidelberg. https://link.springer.com/chapter/10.1007/978-3-031-85960-1_14 Also, invited presentation as a plenary talk at RIPE 89, Prague, Czech Republic
- Walter Gekelman, Patrick Pribyl, Henry Birge-Lee, Joe Wise, Cami Katz, Ben Wolman, Bob Baker, Ken Marmie, Vedang Patankar, Gabriel Bridges, Samuel Buckley-Bonanno, Susan Buckley, Andrew Ge, and Sam Thomas. 2016. Drift waves and chaos in a LAPTAG plasma physics experiment. In American Journal of Physics Volume 84, 118-126. https://doi.org/10.1119/1.4936460
Industry Collaboration
Over the years I have collaborated with many individuals from industry including:
- Let's Encrypt (multiVA/MPIC)
- Google Chrome Root Program (CA/Browser Forum MPIC Ballot SC-067)
- Google Google Trust Services (MPICLabs)
- CloudFlare (MPIC RFC Draft)
- Apple (CA/Browser Forum DNSSEC Ballot SC-085)
- Sectigo (Open MPIC)
- Fastly (dns-persist IETF Internet Draft)
- Amazon (dns-persist IETF Internet Draft)